As a result biba created a model to address the need of enforcing integrity in a computer system.
Biba integrity model example.
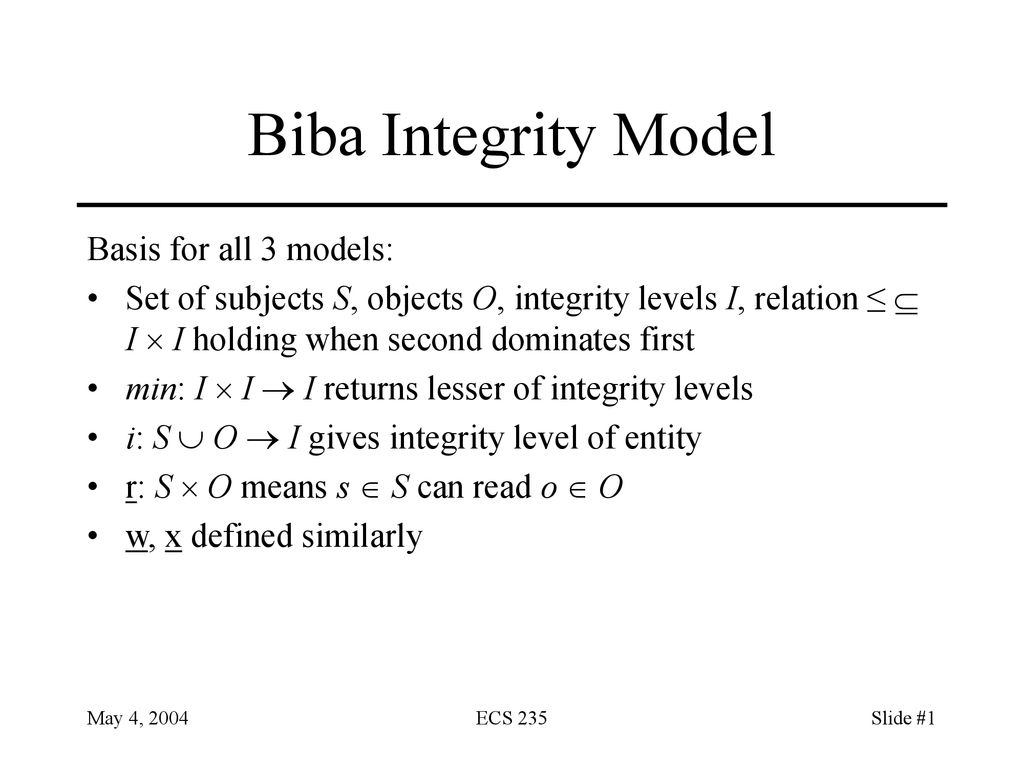
The biba model was the first model developed to address the concerns of integrity.
Clark wilson integrity model.
Originally published in 1977 this lattice based model has two defining properties.
I have read about the ba lapadula blp model of computer security and i managed to understand how it achieves confidentiality through an example can someone explain for me the biba model with an example from an organization of any choice.
It specifies integrity labels on each object in the system which cannot be modified by any operation on the data although a new copy of the object with a different integrity label is possible.
A new label is used to gauge integrity.
Biba in 1977 the biba integrity model sometimes referred to as biba77 was created as a supplement to bell lapadula.
As stated before the bell lapadula model gurantees confidentiality of data but not its integrity.
If a high security object comes into contact with a low level information or be handled by a low level program the integrity level can be downgraded.
This model separates data into one subject that needs to be highly protected referred to as a constrained data item cdi and another subset that does not require high level of protection referred to as unconstrained data items udi.
The biba model or biba integrity model developed by kenneth j.
The primary formal model of integrity the biba model that extends the bell lapadula model incorporates both of these aspects.
3 formal model to show how integrity can be maintained in an optimistic system a formal model is needed that ensures the requirements outlined above are realised by the system.
The biba model addresses the issue of integrity i e.
Simple integrity property this property states that a subject at one level of integrity is not permitted to read an object of lower integrity.
The biba model proposed a.
The biba model focuses on mandatory integrity policies 2.
The model is designed so that subjects may not corrupt data in a level ranked higher than the subject or be.
An example of a workable pessimistic punishment scheme suggested in 1 is to automatically debit a user s bank account when an action is invoked and refund the money if the access is deemed legitimate.
Whether information can become corrupted.
It was the first major security model built to address concerns about system and information integrity and its policies are now implemented in parallel with those of bell lapadula to give a more all embracing assurance of data security.
Cyber attack countermeasures module 1 cyber security safeguards learning objectives recognize the three basic types of cyber security safeguards describe.
Released by kenneth j.